From Substitution to Augmentation: Rethinking AI in Warfare
Roughly two thousand years ago, the full combat load of a Roman legionary weighed approximately 100 pounds (45 kg). Remarkably, modern militaries exhibit a similar pattern. U.S. Army soldiers still carry around 45 kg in full combat gear, while South…
The New Republican Censorship-Industrial Complex
During the Biden administration, public relations writer Michael Shellenberger testified before that House that “American taxpayers are unwittingly financing the growth and power of a censorship-industrial complex run by America’s scientific and technological elite.” This “global censorship-industrial complex” was defined…
Industrial Policy vs. Digital Reality: How Data, Not Labor, Is Rebuilding the Rust Belt
This Palantir advertisement, displayed at the Detroit airport—a symbolic and literal hub of U.S. industrial manufacturing—makes a highly strategic and ideologically charged claim: “Palantir is Reindustrializing America’s Manufacturing.” The ad visually juxtaposes sleek, robotic car manufacturing lines with logos of…
CBDC cryptocurrency Digital Currency Digital Trade Digitization of money General GENIUS Act GENIUS Bill Stablecoin
A GENIUS Bill?
The United States has entered a new chapter in financial regulation with the introduction of the Guiding and Establishing National Innovation for U.S. Stablecoins aka GENIUS Act of 2025. With this, Congress isn’t just attempting to contain crypto, it’s designing…
Is Musk a Hypocrite? Content Removal Cases in Turkiye and India
Since March 19th, 2025, thousands of people in Türkiye have been protesting the government’s arrest of the Mayor of Istanbul. The Mayor, Ekrem Imamoglu, was a presidential candidate backed by the main opposition party (CHP). He might have won an…
New Book: Declaring Independence in Cyberspace
What is the role of the state in the governance of global cyberspace? For the past 25 years, that problem has led to conflict, negotiation and governance innovations. A new book by Milton Mueller now covers a critical part of…
Has the IGF lost the Plot?
The UN Internet Governance Forum will be held June 22-27 in Olso, Norway. The Program Committee for the conference, known as the Multistakeholder Advisory Group (MAG), released its selection of workshops for the 2025 IGF. The number of workshops was…
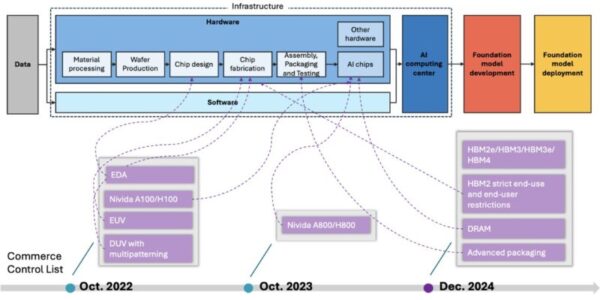
Unpacking US-China “Decoupling” in AI
This is a guest blog from two University of Manchester (UK) doctoral students involved in researching the causal mechanisms linking policy interventions to decoupling outcomes, with implications for innovation ecosystems and global governance. Earlier this year, the release of DeepSeek—an…
“Indigenous” Web Browsers in India: Who Benefits?
Across all three terms, the Modi government has tried to position India as a global technology hub. The state’s strategy involves pursuing self-reliance or “Atma Nirbharta.” The self-reliance strategy is being taken forward through a two-pronged approach — reducing the…
A Review of the Draft Report of the California Working Group on AI Frontier Models
In September 2024, California Governor Gavin Newsom asked prominent researchers at Stanford, UC Berkeley and the Carnegie Endowment to prepare a report to help the State develop responsible guardrails for the deployment of Generative AI. Gov. Newsom’s action followed in the…